Smart Home Cybersecurity for Seniors: Protecting Privacy and Autonomy in Saudi Homes 2025
Comprehensive guide to smart home cybersecurity for seniors in Saudi Arabia. Learn about camera hacking risks, Alexa and Google Home privacy protection, IoT network segmentation, local encrypted storage, and hybrid switch design. Practical solutions for Saudi families.
Introduction: When the Tech Dream Becomes a Nightmare for Parents
In a home in Riyadh's Al-Malqa district, 72-year-old Abu Mohammed sat staring at his smartphone in confusion. His son had converted the entire house to a smart home before traveling abroad: app-controlled air conditioning, voice-controlled lighting, internet-connected security cameras, and a smart lock on the main door. The problem was that the air conditioning stopped working in the middle of Riyadh's scorching summer, and the app was requesting an update he didn't understand how to perform. Abu Mohammed, who had led his company for forty years, found himself unable to turn on an air conditioner in his own home.
This scene repeats daily in thousands of Saudi homes. With the rapid growth of the smart home market in the Kingdom, where voice assistant users like Alexa in Saudi Arabia and the UAE increased by 28% in 2024 alone, a dangerous gap is emerging between the digital generation and the generation that built this nation. This gap is not merely technical ignorance, but a dual threat to cybersecurity and mental health.

Chapter One: The Learn and Forget Phenomenon - Technical Imprisonment at Home
A Saudi study involving 486 elderly individuals conducted by Jazan University in 2022 revealed shocking facts about seniors' adoption of smart technology in the Kingdom. Although 4.19% of the Kingdom's population is currently over sixty, expected to reach 18% by 2050, the adoption rate of smart home technologies among this demographic remains notably low.
Why Do Seniors Fail to Use Technology?
Research identifies several major barriers facing seniors. First is the high cost of smart devices and ongoing cloud subscriptions. Second are technical challenges in setup, maintenance, and continuous app updates. Third are security and privacy concerns that grow with hacking stories. Fourth is difficulty remembering multiple steps to operate each device. Finally, there's the fear of burdening others by asking for help.
The result is what researchers call the Learn and Forget phenomenon. The elderly person learns how to use the app today but forgets the steps after a week. With each instance of forgetting, feelings of helplessness and loss of autonomy accumulate, negatively affecting mental health and self-confidence.
Loss of Autonomy: The High Psychological Cost
The Saudi study found that culture and technology awareness are the most important factors determining seniors' intention to use smart technologies. But more important is psychological attitude. When an elderly person feels they've become completely dependent on their children to operate an air conditioner or turn off a light in their own home, a deep sense of losing control over their environment develops.
In Saudi society that values dignity and independence, this feeling carries special weight. The elderly person who managed businesses and made crucial decisions suddenly finds themselves asking their grandchild to turn on the TV. This shift in family power dynamics has profound psychological effects that cannot be ignored.
Chapter Two: The Open Eye - The Camera Hacking Nightmare
In a society that sanctifies home privacy and considers family privacy a red line, having internet-connected indoor surveillance cameras poses an extremely serious security vulnerability. Stories of home camera hacking and private family photos being leaked are not fiction but documented reality worldwide.
Documented Hacking Incidents
In February 2024, Wyze experienced a breach affecting 13,000 accounts, where users could view photos and videos from other people's cameras without permission. In August 2024, thousands of users reported breaches of their smart devices including cameras and smart locks, where hackers exploited weak passwords and default settings. A recent June 2025 report revealed that over 40,000 security cameras are publicly accessible on the internet, including 14,000 in the United States alone, many accessible with just a regular browser.
Amazon's Ring company faced lawsuits after breaches allowed attackers to speak through cameras and make threats to families. In some cases, hackers demanded ransoms in exchange for not publishing recordings. Google's Nest company was forced to mandate two-factor authentication after a series of breaches.
The Special Risk for Saudi Society
In a traditional Saudi home where women remove their hijab indoors, breaching an indoor camera has catastrophic dimensions beyond mere privacy violation. Leaked images can be used for blackmail or defamation, making protecting these devices not a technical luxury but an urgent social necessity.
Many Saudi families install indoor cameras to monitor elderly relatives, children, or domestic workers. This legitimate use becomes a potential disaster if these cameras are not properly secured.
Voice Assistants: The Polite Spy
Devices like Amazon Alexa and Google Home continuously listen for activation words, but research has revealed serious security vulnerabilities. In 2019, security researchers discovered that both devices could be exploited to eavesdrop on users or trick them into revealing sensitive information like passwords. Third-party applications called Skills can be programmed to continue recording even after the user thinks they've stopped.
In 2018, it was revealed that Amazon employed thousands of contractors to review and transcribe audio recordings from Alexa devices, raising widespread privacy concerns. In 2020, researchers demonstrated the possibility of hacking these devices using laser beams to inject inaudible voice commands from distances exceeding 100 meters.
Chapter Three: Digital Sovereignty - Controlling Your Data
The concept of digital sovereignty means keeping your data under your complete control, not stored on servers in other countries that may not be subject to laws protecting your privacy. In the context of smart homes, this means making conscious decisions about where your recordings are stored and who can access them.
Local Encrypted Storage Instead of Cloud
Instead of uploading camera recordings to external servers, they can be stored locally in your home. NVR or Network Video Recorder systems store recordings on hard drives inside a device in your home, meaning no one can access them remotely except you. Local storage on SD cards inside the camera itself is a simpler and cheaper option, with some cameras supporting cards up to 512 gigabytes.
End-to-End Encryption means recordings are encrypted from the moment of capture until viewing, and even the service provider cannot decrypt them. Companies like Haicam, Eufy, and Arlo have started offering this feature. Ring cameras added full encryption after breach scandals.

Cameras Without Cloud Subscription
Many companies charge monthly subscriptions for cloud storage, but there are excellent alternatives. Tapo cameras from TP-Link work without subscription with local SD storage. Eufy cameras offer local storage on HomeBase with encryption. Reolink cameras provide integrated NVR systems with hard drives up to 2 terabytes. Arlo Pro 5 cameras support local storage on hub with capacity up to 2 terabytes.
These options eliminate the need for monthly subscriptions and keep your recordings inside your home, away from prying eyes.
Chapter Four: Network Segmentation - Digital Fortresses Inside Your Home
One of the most important cybersecurity strategies for smart homes is separating the IoT device network from the personal device network. The idea is simple: if someone hacks your smart camera, they shouldn't be able to jump from it to your phone or personal computer.
What Are VLANs?
Virtual Local Area Networks are technology that allows dividing one physical network into several logically separate networks. Each network is isolated from the other as if they were in different buildings, although they use the same router and cables.
Ideal Smart Home Segmentation
Optimal segmentation includes three separate networks. The first is the Personal Network containing phones, computers, and tablets, the most protected as it contains your sensitive data. The second is the IoT Network containing smart TVs, air conditioners, refrigerators, and smart home appliances, isolated because these devices are often less secure. The third is the Camera Network containing surveillance cameras and NVR devices, completely separated as the most sensitive.
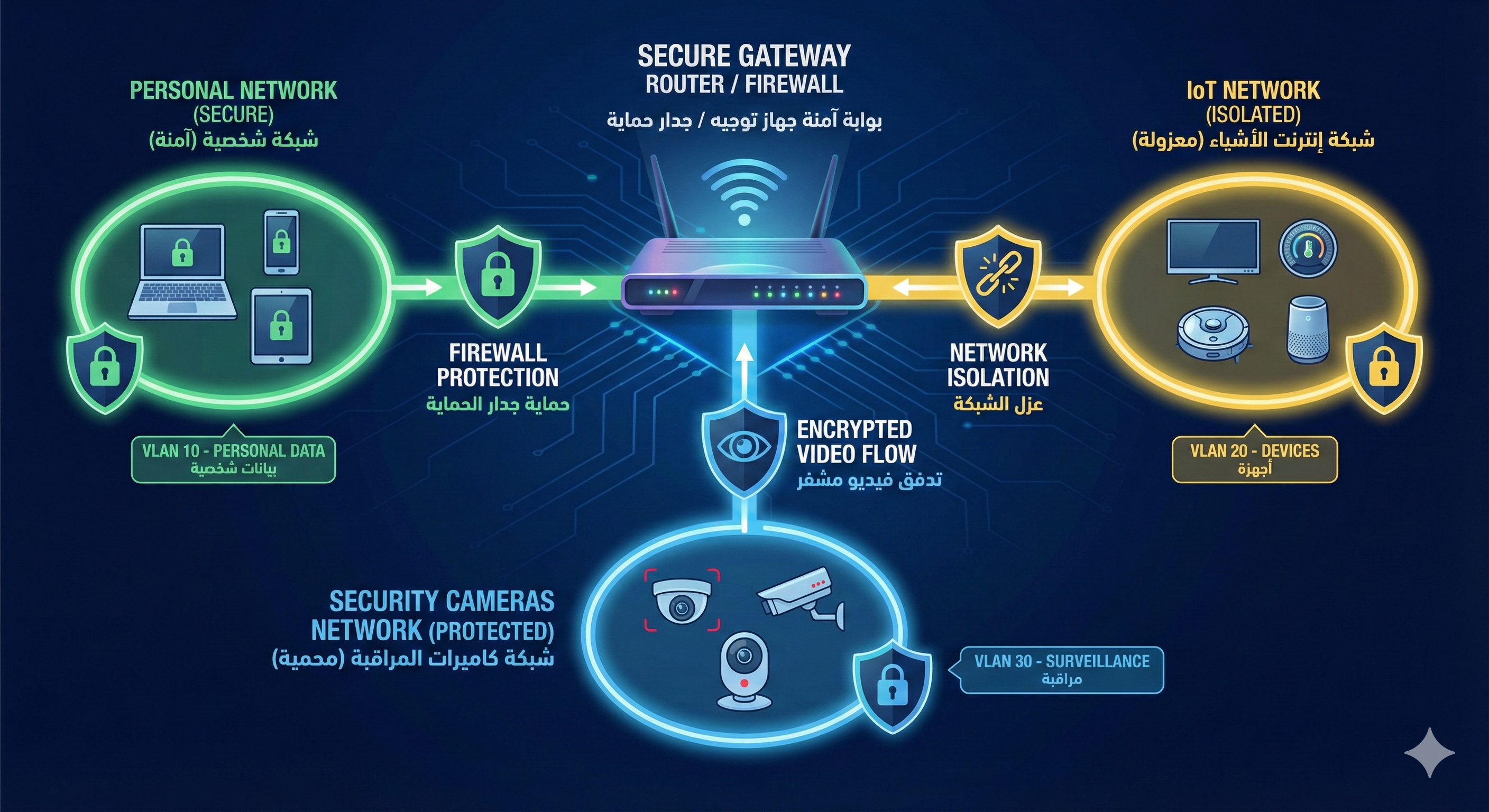
Firewall Rules Between Networks
After creating separate networks, you need rules governing communication between them. IoT devices are prohibited from initiating connections to the personal network. The personal network is allowed to access IoT devices to control them. The camera network is completely isolated and doesn't communicate with any other network. The guest network is separate with no access to internal resources.
This design means that even if someone hacks your smart TV, they won't be able to access your photos or personal files on your phone.
Required Equipment
To implement this segmentation, you need a router that supports VLAN like Ubiquiti, Netgear, or routers running OpenWrt or pfSense. You also need a smart switch supporting the 802.1Q standard like TP-Link TL-SG105E costing about 120 SAR. Plus a WiFi access point supporting multiple SSIDs for each VLAN.
Total cost to upgrade a regular home network to a segmented network ranges from 500 to 2000 SAR depending on home size and equipment quality.
Chapter Five: Hybrid Design - Smart and Physical Switches Together
The optimal solution for Saudi homes with elderly residents isn't abandoning technology, but hybrid design combining AI advantages with traditional control simplicity.
The Double Backup Principle
Every smart device should have an alternative physical control method. Smart switches should contain physical buttons that work even without WiFi or an app. Smart air conditioners should retain a traditional infrared remote. Smart locks should support traditional keys as a backup option.

Why Is Manual Control Necessary?
When internet or WiFi is interrupted, smart switches that depend entirely on the app become useless. When forgetting a password or phone malfunction, the user loses ability to control their home. For seniors who find apps difficult, the physical button is the intuitive solution. In emergencies, there's no time to search for the phone and open the app.
Smart Switches with Manual Control
Iotics Smart Switches come with physical buttons that work in all conditions. Jasmine Smart Switches support manual operation and local scheduling even without internet. Kasa switches from TP-Link retain a manual button on the device itself. Most good modern smart switches support what's called Manual Override.
Installation Tips for Homes with Seniors
Keep traditional switches in the most frequently used places like bedrooms, kitchens, and bathrooms. Smart switches can be installed in living rooms and hallways. Train seniors on using the physical button first, making the app a secondary option. Place simple explanatory labels on smart switches.
Chapter Six: Protecting Voice Assistants
If you decide to use Alexa or Google Home, there are essential steps to reduce risks.
Basic Privacy Settings
Enable two-factor authentication on your account. Review and delete voice recordings periodically from privacy settings. Disable continuous listening feature if possible. Don't connect sensitive devices like locks and cameras to the voice assistant. Use a voice PIN for purchases and sensitive commands.
Physical Device Placement
Don't place the voice assistant in bedrooms or private areas. Avoid placing it near windows where external sounds or even laser beams could manipulate it. Keep it away from TVs and radios that might accidentally activate it.
The Local Alternative
For families very concerned about privacy, there are open-source alternatives like Home Assistant with Rhasspy for completely local voice control without any connection to external servers. This requires more technical knowledge but provides complete digital sovereignty.
Chapter Seven: Security Audit Checklist for Saudi Smart Homes
Before Purchase
Ensure the device supports manual or physical control. Check the privacy policy and storage server locations. Choose devices supporting local storage or full encryption. Avoid cheap devices from unknown brands. Ensure continuous security update support exists.
During Installation
Change the default password immediately to a strong, unique one. Enable two-factor authentication on all associated accounts. Create a separate network for IoT devices if possible. Disable UPnP feature on the router as it creates security vulnerabilities. Record all devices and their information in a safe place.
Ongoing Maintenance
Update device firmware regularly or enable automatic updates. Review access logs periodically to detect suspicious activity. Change passwords regularly especially after any announced breach of the manufacturer. Check devices connected to your network and remove any unknown device.
Chapter Eight: Costs and Solutions Table
Camera Protection
Camera with local SD storage ranges from 150 to 400 SAR. NVR system with 4 cameras and 2TB drive ranges from 1500 to 4000 SAR. 256GB SD card costs about 100 SAR.
Network Segmentation
Smart switch supporting VLAN like TP-Link TL-SG105E costs about 120 SAR. Advanced router supporting VLAN ranges from 400 to 1500 SAR. WiFi access point supporting multiple SSIDs ranges from 200 to 600 SAR.
Hybrid Switches
Smart switch with manual button ranges from 80 to 200 SAR. Backup traditional remote for smart AC ranges from 50 to 150 SAR. Smart lock with traditional key ranges from 400 to 1200 SAR.
Frequently Asked Questions
Can surveillance cameras be hacked even with a strong password?
Yes, if the manufacturer itself experiences a breach. This is why local encrypted storage is better than cloud storage.
My parents can't use apps, is a smart home suitable for them?
Yes, if you choose devices with manual control and make the app for remote management only. Your parents use buttons, and you monitor and manage remotely.
Does Alexa record everything I say?
Officially, it only records after the activation word. But activation errors occur, and you can review and delete recordings from settings.
How much does it cost to fully secure a smart home?
Basic security starts from 500 SAR with password changes and device updates. Medium security with network segmentation ranges from 1500 to 3000 SAR. Advanced security with NVR and full encryption ranges from 5000 to 10000 SAR.
Is it better not to buy smart devices at all?
No, smart technology has real benefits especially for monitoring seniors, energy saving, and security. The key is conscious selection and proper security.
Conclusion: Balance Between Intelligence and Wisdom
The smart home is not inherently evil, but it's a double-edged sword requiring awareness and wisdom in use. In the Saudi context, where family privacy values intersect with rapid digital transformation, we need a balanced approach that respects seniors and protects family privacy.
Solutions exist: local encrypted storage, separate networks, devices with manual control, and continuous awareness of risks. Investing in these solutions today protects your family from tomorrow's nightmares.
Always remember: technology should serve you, not enslave you. And the sanctity of the Saudi home is a red line that no technology should cross.
